Customer Logins
Obtain the data you need to make the most informed decisions by accessing our extensive portfolio of information, analytics, and expertise. Sign in to the product or service center of your choice.
Customer LoginsBriefCASE: New security regulations pose challenge for automakers
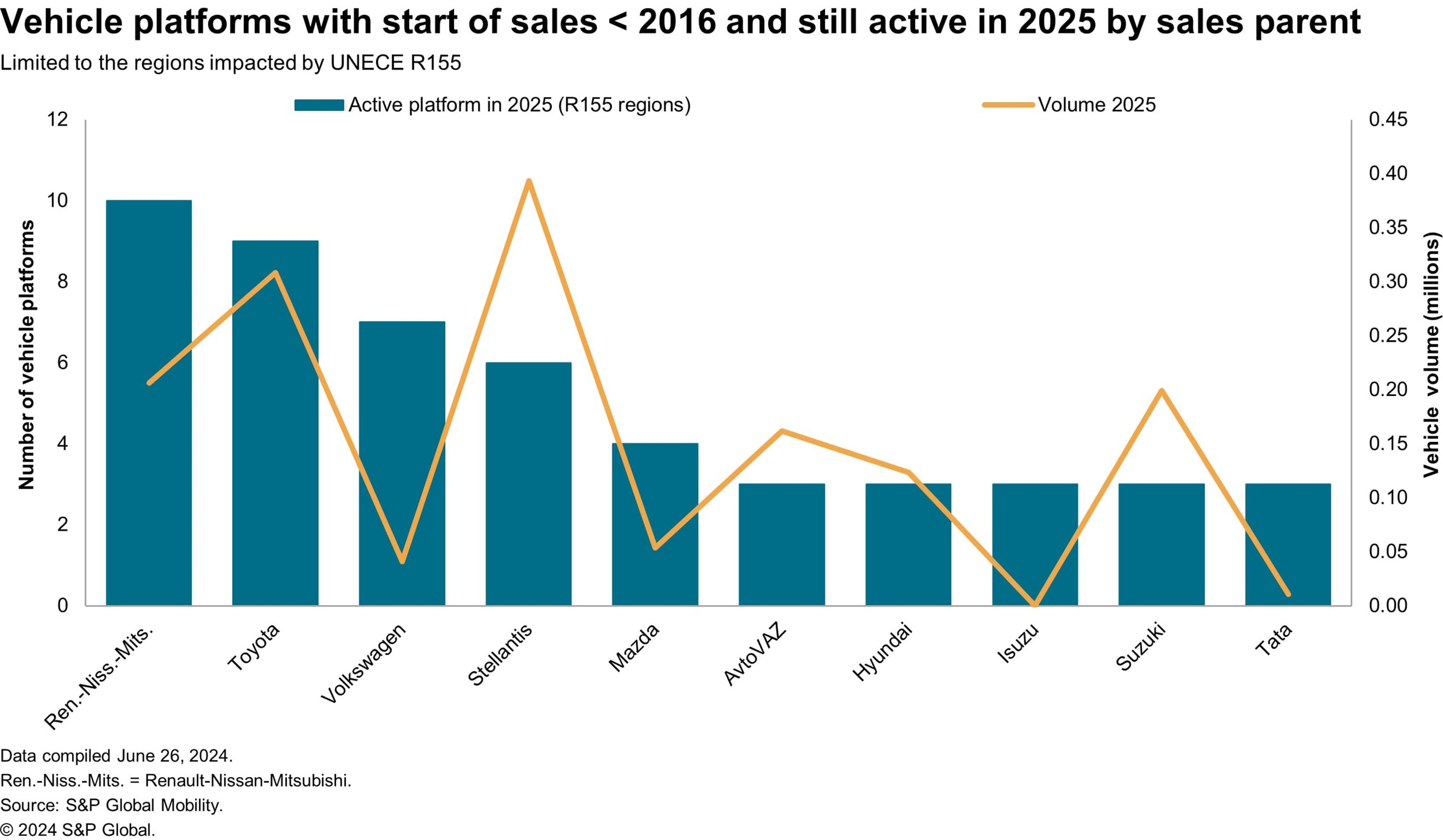
UNECE R155 is probably not top of mind for most casual observers of the automotive industry. However, for those within it is generating plenty of discourse and generating fundamental questions as to what original equipment manufacturers' future competencies should be. For those outside the industry, the nearest encounter with R155 could be the news that Porsche ceased the sale of its internal combustion engine (ICE) Macan in Europe early in 2024 because of compliance issues. Because of this one could be forgiven that it is another electric vehicle mandate. But no, R155 is all about cybersecurity. Not just cybersecurity at a vehicle's start of production, but throughout its end-to-end life cycle. The increasing connectivity of vehicles is bringing more vulnerabilities. A mini-industry has sprung up that exposes the frailties of today's cars through a series of audacious hacks. Among the famous hacks are the example of the Nissan Leaf in the north of England being remotely controlled from a poolside in Australia or Tencent's Keen Security Lab hack of Tesla models back in 2016. R155 is designed to lessen the frequency of such incidents. The regulation requires systematic measures such as regular risk assessments, penetration tests and robust incident response mechanisms to mitigate cyberthreats. The regulation also emphasizes a secure software update management system to maintain vehicle safety with up-to-date software. The R155 regulation* has implications beyond in-vehicle considerations, requiring extensive organizational effort and potentially high costs. Managing risk throughout the vehicle life cycle can be challenging, particularly for traditional OEMs with a wide range of vehicle models. Consequently, OEMs are now focused on embedding security into vehicle design and ensuring compliance to avoid penalties and withdrawal of vehicle homologation. The transition to a compliant Cybersecurity Management System (CSMS) presents challenges and cost considerations for OEMs. In a recent estimation by S&P Global Mobility, the costs of compliance for two vehicles designed with older design distributed E/E architectures were calculated for an A-segment vehicle and a premium D-segment vehicle. The implementation costs on existing models can easily exceed $1 million even for the A-segment vehicle with fewer features. Thus, withdrawing vehicles from sale that are approaching end of life or are sold in low volume makes perfect sense. Thus far, the Porsche Macan has been the only vehicle officially retired because of R155 and there has been much speculation in the press with nine specific vehicles widely cited as impacted. To verify the reports, we sought the counsel of colleagues in S&P Global Mobility's production forecasting division. Based on this, we can confirm that of the nine vehicles reported, five are specifically impacted by the R155 regulation. The affected vehicles are three Porsche models (Boxster, 718 Cayman and Macan) and two Audi models (R8 and TT). None of these models will continue to be sold in Europe owing to the regulation. However, sales of these vehicles may continue in regions outside of Europe that are not subject to the legislation. In the midterm, OEMs cannot discontinue all legacy platforms, however, and they must bear the cost of making vehicles compliant, especially high-volume platforms that are planned to continue for several years. The following chart displays the relative exposure of OEMs to these "retrofit" compliancy costs. It shows the number of platforms still in production in 2025 with SOP earlier than 2016, i.e., before most OEMs started considering cybersecurity in design.
However, OEMs are less tactical and are rethinking the way they design vehicles as they make them software-defined vehicle (SDV)-ready. Deploying SDV-ready vehicles supported by advanced E/E architectures, particularly centralized zonal architecture that can deploy software updates seamlessly, avoids the costly retrofitting. They also ensure compliance with regulations as the system-on-a-chip (SoC) powering them are equipped with embedded crypto and security functions compliant with R155. As with the SDV and many of the other industry megatrends, cybersecurity has brought a lot of navel-gazing among industry participants. There are fundamental questions to answer as to what the core competencies of the OEMs and tier 1s should be in the future. They are unsure, for example, whether software development and SDV stacks should rely on outsourcing or to keep certain aspects in-house. How to add cybersecurity compliance may also present conflicts with an OEM's chosen software path on the fundamental make or buy decision. The company that has chosen the make path may find hidden costs with cybersecurity compliance such as adding in-house expertise and the cost of operating Security Operation Centers in-house. Either way, R155 and cybersecurity obligations are posing new challenges that need to be addressed. While there may be headlines about production runouts in Europe, the focus is on navigating these new roadblocks. *Adopted by the United Nations Economic Commission for Europe (UNECE), the UN R155 became effective in January 2021. This regulation mandates that all new vehicle types must comply starting from July 2022, and all vehicles produced must comply by July 2024. |
This article was published by S&P Global Mobility and not by S&P Global Ratings, which is a separately managed division of S&P Global.