Featured Topics
Featured Products
Events
S&P Global Offerings
Featured Topics
Featured Products
Events
S&P Global Offerings
Featured Topics
Featured Products
Events
S&P Global Offerings
Featured Topics
Featured Products
Events
Financial and Market intelligence
Fundamental & Alternative Datasets
Government & Defense
Professional Services
Banking & Capital Markets
Economy & Finance
Energy Transition & Sustainability
Technology & Innovation
Podcasts & Newsletters
Financial and Market intelligence
Fundamental & Alternative Datasets
Government & Defense
Professional Services
Banking & Capital Markets
Economy & Finance
Energy Transition & Sustainability
Technology & Innovation
Podcasts & Newsletters
13 Sep, 2022

|
A power facility in Texas. |
As the U.S. works to shore up funding for cyber protections in its 2023 defense bill, security experts warn that critical infrastructure remains vulnerable.
More than six months since the U.S. Cybersecurity and Infrastructure Security Agency, or CISA, issued a heightened cybersecurity alert for organizations, security experts and industry executives say more detailed guidance and standardization is needed to better safeguard potential U.S. targets. That may require more investment from both public and private sources, they note.
"We see this as climbing a ladder of maturity in terms of cyber protection, and a lot of the critical operations are starting at the bottom of the ladder," said Duncan Greatwood, CEO of Xage Security Inc., a security services company that helps critical infrastructure companies meet cybersecurity compliance.
Russia's invasion of Ukraine in February led to an array of sanctions that many believed would trigger Moscow to retaliate via cyber warfare against American services. CISA responded by advising organizations to be ready to detect unusual network behavior and to ensure their software was up-to-date, among other recommendations. Wall Street expected the conflict would catalyze increased investment in domestic cybersecurity services and companies including CrowdStrike Holdings Inc. and Palo Alto Networks Inc.

Vulnerability assessment
While security experts have pointed to signs of progress since then, they said more needs to be done to prepare for potential cyberattacks.
CISA's alert in mid-February should have been followed by more detailed directives from sector risk management agencies, Greatwood said. But such directives have been rare.
As an example of the type of follow-through that is needed more widely, Greatwood pointed to the Transportation Security Administration's oil and natural gas pipeline security directives, released in July. The directives required TSA-specified owners and operators of pipeline and liquefied natural gas facilities to move toward developing network segmentation policies and controls to ensure that operational technology systems could continue to safely operate even if related information technology systems are compromised. The facilities were also told to take measures to prevent unauthorized access to critical cyber systems.
Additionally, CISA's messaging needs to be updated to avoid "vigilance fatigue," security experts said.
CISA Director Jen Easterly and National Cyber Director Chris Inglis recently acknowledged the risk of vigilance fatigue in an op-ed published in June, saying, "While we will never stop defending cyberspace, maintaining a maximum alert posture is not sustainable over a long period of time." The op-ed called for continued collaboration between the government and private sector, as well as a new cyber alert advisory framework that would succeed the agency's current approach.
The federal government also could help fund and direct the implementation of protections for small infrastructure players who cannot afford services that meet current cybersecurity standards, security experts told S&P Global Market Intelligence.
The National Defense Authorization Act, or NDAA, a yearly defense funding bill that sets the annual budget of U.S. defense agencies, includes a list of provisions that would strengthen cybersecurity capabilities. The bill is necessary legislation to fund the U.S. military and related agencies, and Congress faces a Sept. 30 deadline to pass it before the end of the fiscal year.
Lauren Zabierek, executive director of the Cyber Project at Harvard University's Belfer Center, told Market Intelligence that she hopes the funding and guidance set out in the bill will lead to protection requirements for devices embedded into industrial control systems, such as sensors and actuators.
Internet-connected industrial control systems are not currently required to have baseline protections, Zabierek said. The NDAA includes industrial control systems training but does not mandate protections for internal controls.
Attack parameters
Though U.S. infrastructure has not suffered a major cyberattack from Russian-backed or Russian-tolerated sources following the Ukraine conflict to date, it would be a mistake for American businesses and policymakers to drop their guard, experts say.
Even if the Russian government had already used offensive cyber techniques earlier this year, sympathetic splinter groups may step in to launch their own attacks, said Gavin Wilde, a senior fellow at the Carnegie Endowment for International Peace specializing in Russian information warfare.
Scott Jasper, a senior lecturer at the Naval Postgraduate School and author of Russian Cyber Operations: Coding the Boundaries of Conflict, said ransomware attacks similar to that carried out last year against the Colonial Pipeline are still possible. That attack lead to a shutdown and restart of the targeted U.S. pipeline system and caused temporary gas shortages in parts of the country.
U.S. policymakers should standardize the adoption of extended detection and response frameworks, or XDR, to prevent such ransomware activities, Jasper said. XDR is a practice that consolidates digital security data to actively monitor network threats.
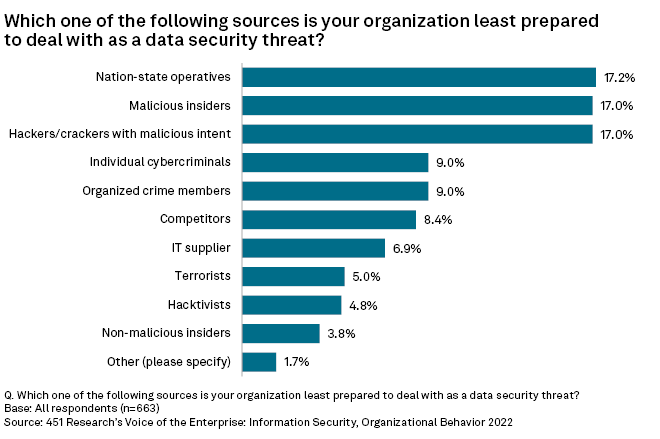
A 451 Research report titled "Voice of the Enterprise: Information Security, Organizational Behavior 2022" published this month found that surveyed IT end-user decision-makers felt least prepared to deal with nation-state actors organizing data security threats. A separate report authored in August said ransomware continues to be a key concern for enterprise chief information security officers.
Critical mandates
The expense associated with investing in robust protections is often cited as a reason for delay by some organizations. That is where regulations are needed to ensure a base level of safeguards, security experts said.
"In our experience, healthcare and even energy do what they have to do because someone tells them they have to do it," said David Stone, sales director at WinMill Software Inc, a technology consulting firm offering cybersecurity services.
Even strong mandates can fall short due to unforeseen flaws, said Scott Crawford, a security operations analyst at 451 Research. At a minimum, it would be in policymakers' best interest to coordinate any directives with major security providers, the analyst said.
WinMill's Stone said regulators should consider subsidizing costs to integrate needed critical protections while also standardizing those protections at a federal level.
Unfortunately, the biggest motivator for critical operators is often a direct attack, Crawford said. While there have been prior incidents that brought more attention to the need for infrastructure protection, it may take another attack before some of them get done, he noted.
"Do we have to have more incidents before it becomes a more prevalent thing? ... History would suggest that we do," Crawford said.
451 Research is part of S&P Global Market Intelligence.
