U.S. agencies are still working to address blind spots in federal pipeline cybersecurity programs at a time when analysts and the government are issuing warnings about threats from Iranian hackers.
The warnings follow a U.S. airstrike that killed Islamic Revolutionary Guard Corps commander Gen. Qassem Soleimani. The U.S. Cybersecurity and Infrastructure Security Agency on Jan. 6 issued an alert in light of escalating tensions between Washington, D.C., and Tehran, noting that Iran has been linked to cyber operations targeting a range of industries, including energy, as well as several high-profile attacks.
Dragos, a cybersecurity firm focused on critical infrastructure, identified a "recent increase in activity targeting" the North American energy sector in a Jan. 8 report. The firm pointed to attempts by alleged state-sponsored Iranian hackers to breach the oil and gas industry and the electric sector. "[I]ncreased activity coincides with rising escalations between the U.S. and allies, and Iran in the Middle East," the firm said. "Dragos expects this activity to continue."
The U.S.'s lead agency for pipeline cybersecurity, the Transportation Security Administration, has long struggled to keep up with some of its oversight obligations. The TSA, which provides security guidelines to pipeline operators and conducts reviews of their operations and facilities, is still addressing deficiencies in its Pipeline Security Program flagged by the Government Accountability Office in a December 2018 report.
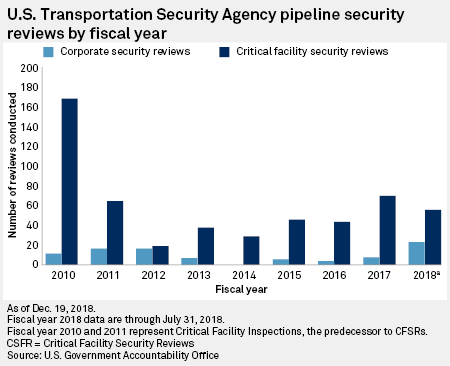
The GAO's 2018 report found weaknesses in the TSA's process for issuing security guidelines, its approach to staffing and the way it assesses risk to prioritize pipeline system reviews. The GAO also found that the TSA lacks a formal system to follow up on and assess the effectiveness of security recommendations to pipeline operators.
The GAO issued 10 recommendations to improve the TSA's pipeline security program. The agency has fully implemented one of them, so far.
TSA staff dedicated to pipeline cybersecurity has fluctuated from 14 full-time equivalents to as few as one in recent years, limiting the agency's ability to carry out security reviews, according to the GAO. As recently as last year, none of the employees working on the issue had cybersecurity expertise.
Amid the struggles, Rep. Emanuel Cleaver, D-Mo., is seeking to codify the TSA's lead cybersecurity role into law through the Pipeline Security Act. The legislation introduced in July 2019 addresses several GAO recommendations, including regularly updating industry guidelines, developing a personnel strategy and recruiting cybersecurity experts.
The threat
Dragos has listed a so-called systemic attack that targets natural gas pipelines — and the related cascades through the electric power or gas distribution system — among its concerning possible attack scenarios for North America.
Analysts say it currently appears unlikely that Iran has the ability or motivation — unless directly provoked — to launch such an attack, but the recent attempts to breach energy industry defenses demonstrate an ongoing attempt to develop new capabilities.
"Over time Iran has improved its cyber capabilities, reduced its response time and shown it is capable of strategic surprise. This is especially a problem with Iran because of their peculiar sense of symmetry. Anything we do to Iran, Iran is likely to do back at us," Tom Warrick, an Atlantic Council fellow and former U.S. deputy assistant secretary for counterterrorism policy at the Department of Homeland Security, said during a Jan. 15 congressional hearing.
Alternate oversight
With the nation's electric grid growing more dependent on natural gas supply, the GAO assessment underscored efforts to shift responsibility for pipeline cybersecurity to the U.S. Department of Energy. Backers of the idea include Federal Energy Regulatory Commission Chairman Neil Chatterjee and Commissioner Richard Glick.
"I continue to have serious concerns about the TSA's ability here," Glick told the House Energy and Commerce Committee's Energy Subcommittee in June 2019.
The DOE has been shoring up its cyber resources for the last two years, opening the Office of Cybersecurity, Energy Security, and Emergency Response in February 2018 and the Office for Artificial Intelligence and Technology in September 2019.
Efforts by Rep. Fred Upton, R-Mich., the ranking member of the Energy Subcommittee, to codify the DOE's growing role in pipeline cybersecurity through the Pipeline and LNG Facility Cybersecurity Preparedness Act have made progress in both chambers of Congress. His bill would put the DOE in charge of coordinating interagency cooperation on pipeline security and leverage its expertise in energy to advance cyber protections.
The legislation would not tackle minimum cybersecurity standards for pipelines like those imposed on U.S. electric power systems in 2009.
Chatterjee and Glick support minimum cybersecurity standards for pipeline operators. Glick testified during the June 2019 hearing that a TSA official earlier told him the agency hopes to achieve an 80% adoption rate for its voluntary pipeline security guidelines.
"80% doesn't cut it. We need 100%," Glick said.



