Featured Topics
Featured Products
Events
S&P Global Offerings
Featured Topics
Featured Products
Events
S&P Global Offerings
Featured Topics
Featured Products
Events
S&P Global Offerings
Featured Topics
Featured Products
Events
Financial and Market intelligence
Fundamental & Alternative Datasets
Government & Defense
Professional Services
Banking & Capital Markets
Economy & Finance
Energy Transition & Sustainability
Technology & Innovation
Podcasts & Newsletters
Financial and Market intelligence
Fundamental & Alternative Datasets
Government & Defense
Professional Services
Banking & Capital Markets
Economy & Finance
Energy Transition & Sustainability
Technology & Innovation
Podcasts & Newsletters
13 Jun, 2022
|
Big Tech companies are working with industry standards organizations to expand support for a password-less security option. |
A tech industry coalition including Apple Inc., Alphabet Inc. and Microsoft Corp. is working to expand adoption of a secure alternative to the common password.
Under agreements struck this year, a new standard known as FIDO, short for Fast IDentity Online, will be built into major operating systems such as macOS, iOs, Windows 11, Chrome OS and Android in the coming months. Users will have the choice to opt in to the new protocols, which will allow them to log in securely without a password.
Apple demonstrated how FIDO-authorized passkey technology is integrated into its new macOS Ventura and iOs 16 at its Worldwide Developers Conference on June 7.
"Now is the time to adopt them [passkeys]," said Garrett Davidson, an authentication technology engineer at Apple. "Not only is the user experience better than a password, but ... weak and reused credentials, credential leaks and phishing are just not possible anymore."
Proponents of the new standards say they offer a less hackable alternative to passwords by relying on bits of encrypted code stored on paired devices and will reduce overall security costs. In adding support for the standards on major operating systems and search engines, tech companies will make it easier to access the new security credentials without having to reenroll multiple accounts.
"For the user, it will be a big win, in that the complexity of the protocol is hidden from them," said Johannes Ullrich, dean of research at the SANS Technology Institute, an organization specializing in cybersecurity research and education. "It's one of the few authentication standards that really tries to balance privacy and authentication."
Some caution, however, that start-up costs and technical education could prove a hurdle for small businesses and websites considering upgrading their systems to the new standard.
How it works
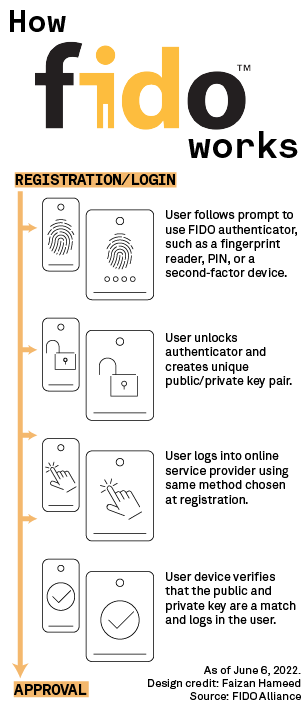 |
FIDO authentication protocols enable users to use their mobile device to sign into an app or website on another nearby device, regardless of the operating system or browser they are running.
The authentication method uses public key cryptography to scramble and encrypt user data that can only be accessed in tandem with a private key, which is stored on a user's device. Secondary devices using the standard are unlocked using a biometric tool like facial recognition or a fingerprint scan to enable communication between devices.
"A lot of people are used to the friction of a password," said Andrew Shikiar, executive director and chief marketing officer at FIDO Alliance, the nonprofit coalition working to develop and deploy the new standards. "Ultimately, the best authentication is the authentication you don't know you're using."
Tests of password-less authentication standards at companies including Microsoft, Google, Intuit Inc. and T-Mobile US Inc. indicated successes in reducing phishing attacks, according to studies by FIDO Alliance and partner Nok Nok Labs, a software developer that provides online authentication solutions for organizations.
Adoption outlook
Big Tech's cooperation is expected to help the new standard catch on. Apple's Touch ID and Face ID, for example, helped to popularize biometrics.
The average total cost of a data breach was $4.24 million in 2021, up 10% year over year, according to a report from International Business Machines Corp. and the Ponemon Institute, a research center focused on privacy, data protection and information security policy. Businesses are looking for ways to improve security and reduce the financial and reputational risks associated with a breach.
Many of Microsoft's customers view the transition to password-less authentication as a priority to reduce IT costs and save time troubleshooting security concerns, said Alex Simons, corporate vice president of product management of Microsoft's Identity and Network Access Division. But challenges remain even for those eager to make the shift.
"Among the biggest hurdles we've seen are internal resistance to change, inertia, and sheer scale of moving entire organizations to use password-less technologies," Simons said.
Start-up costs also could prove an initial barrier to some businesses or website managers, said the SANS Technology Institute's Ullrich.
Revamping a website to operate in accordance with FIDO protocols could cost more than $10,000, and most companies will pay about $50 per user to add an employee's authenticator token into their system, Ullrich estimated.
Still, Ullrich expects high-risk enterprises like fintech entities and online banks to begin rollouts of the FIDO standards within the next year.
"When service providers choose to roll out a FIDO deployment, they typically implement incrementally to ensure and test for usability and functionality," said FIDO Alliance's Shikiar. They can choose to build their own software implementation or license the technology from a certified vendor or host.
Some online retailers or e-commerce websites may find outsourcing security features such as payment processing to large enterprises is more practical than building more-secure features themselves, said Kurt Seifried, chief blockchain officer and director of special projects at Cloud Security Alliance.
"The biggest thing that's going to happen to actually improve security is when people move to the large providers," Seifried said. "You can't have a Mom and Pop doing it. You need somebody like Amazon or Shopify or Google doing it."
Breaches caused by compromised credentials account for nearly 20% of global security breaches surveyed in the IBM/Ponemon study. At the enterprise level, businesses could save between $30 million and $40 million in cybersecurity operating expenses annually by switching to more secure password-less technology, said Larry Ponemon, chairman and founder of the Ponemon Institute.
"[Password-less authentication] has tremendous potential, because if you do this right, ensuring high integrity, you have better results with your customers," Ponemon said.
Obstacles
Downsides to password-less standards include adding uncertainty about the customer experience for some users.
"Biometrics … involve measurement and measurements are prone to errors," said Garrett Bekker, principal information security analyst at 451 Research. "If you're going to use [facial recognition] and have some technology that's going to do a sample of my face, it's not a binary yes or no. So you have to choose — what degree of uncertainty are you willing to live with?"
Users with cognitive or physical disabilities could face accessibility hurdles, said Cloud Security Alliance's Seifried.
"My concern is that if we force people to use FIDO tokens, what happens to the people who can't?" Seifried said.
Widespread adoption is also dependent on interoperability across competing systems. Microsoft's Simons said new FIDO standards take this into account with the development of multi-device credentials, or passkeys, which can be used to authenticate across Android, Chrome OS, iOS, macOS and Windows. Apple and Alphabet did not respond to requests for comment.
Other hurdles include the limitations of existing infrastructure that might need to be upgraded to support the new technology.
"There's a lot of legacy client server apps and mainframes that are still in use by a lot of enterprises and they probably will be for a very long time," Bekker said.
The new protocols are more likely to be additive as opposed to direct replacements in the early stages of the adoption curve, said Jon France, chief information security officer of (ISC)², a nonprofit that provides training and certifications for cybersecurity professionals.
"Early adopters are great, but it's the mainstream you want," France said. "Getting used to multifactor authentication took a while. People still get upset when it comes to SMS or pin numbers."
451 Research is part of S&P Global Market Intelligence.
