Featured Topics
Featured Products
Events
S&P Global Offerings
Featured Topics
Featured Products
Events
S&P Global Offerings
Featured Topics
Featured Products
Events
S&P Global Offerings
Featured Topics
Featured Products
Events
Financial and Market intelligence
Fundamental & Alternative Datasets
Government & Defense
Professional Services
Banking & Capital Markets
Economy & Finance
Energy Transition & Sustainability
Technology & Innovation
Podcasts & Newsletters
Financial and Market intelligence
Fundamental & Alternative Datasets
Government & Defense
Professional Services
Banking & Capital Markets
Economy & Finance
Energy Transition & Sustainability
Technology & Innovation
Podcasts & Newsletters
3 May, 2022
By Zoe Sagalow and Umer Khan
Banks must begin complying with a new rule that requires them to report certain computer security incidents to regulators within 36 hours, a reporting time frame that could prove challenging, especially for smaller companies.
The rule, issued jointly by the Federal Deposit Insurance Corp., Office of the Comptroller of the Currency and Federal Reserve Board of Governors, calls for reports to regulators via phone, email or similar methods. Although the rule took effect on April 1, banking organizations and bank service providers must comply by May 1.
The 36-hour time frame is relatively short because, in most cases, regulators tended to allow at least a couple of days for reporting, said David Murphy, manager of cybersecurity at Schneider Downs & Co. Inc. For smaller banks, handling both reporting and managing the problem itself could be a challenge because of fewer people and resources.
"If you're a small bank, and you have a small IT team, you're going to want your IT team focused on dealing with the incident, not necessarily the details around reporting what's happened," Murphy, who helps banks with security, said in an interview.
The banking regulators, along with state and other federal regulators, are increasing pressure to report cyber incidents as much as possible, he said.
"Prior to all these rules, there was basically no incentive to report that you had some type of computer-related incident, and that causes problems," Murphy said. "It basically causes issues with us understanding the scope of the problem."
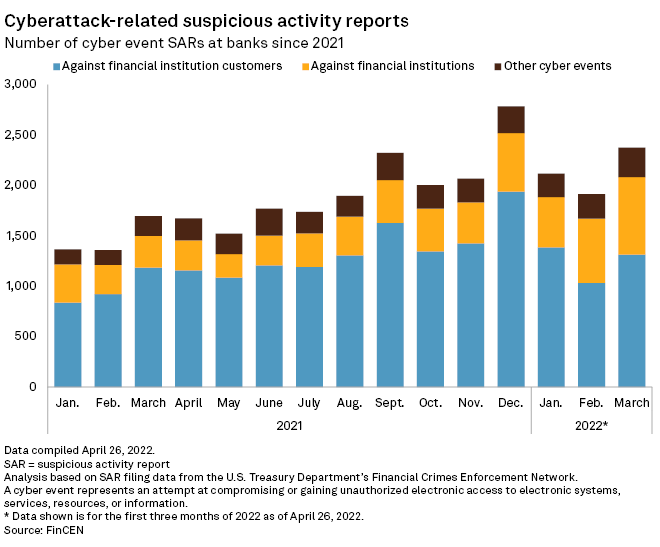
There has been a rise in ransomware over the past 18 months, said Julie Bernard, principal with Deloitte's cyber and strategic risk team. For bigger banks, which Deloitte works with most, this requirement is "an update to their standard incident response plans. Not a huge update, but what they have to figure out is: Who are the various regulators they need to report to? … They're already doing reporting anyway to other industry groups."
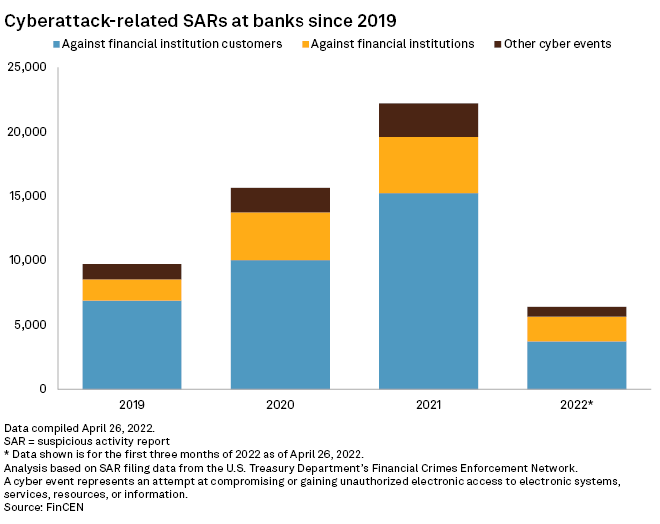
Banks are already required to file suspicious activity reports no more than 30 days after initially finding information that may be a basis for a report, and those reports are not all related to cybersecurity. The new rule also applies to certain bank service providers. Under the rule, they need to report to their banking organization customers "as soon as possible when the bank service provider determines that it has experienced a computer-security incident that has caused, or is reasonably likely to cause, a material service disruption or degradation for four or more hours."
Financial institutions might notify more rather than less to maintain regulatory relationships, and the rules are written about generally significant incidents anyway, said Michael Borgia, partner leading the information security group at Davis Wright Tremaine LLP.
"We're not going to try to parse out all the fine points of when you have to notify and when you don't, within reason," Borgia said in an interview, describing the perspective of most financial institutions he has spoken with. "We're going to be inclined to notify because maintaining that relationship is very valuable to us, and trying to come up with clever arguments for why we shouldn't have to notify just doesn't make sense in the long run, really."
Reporting requirements for service providers
Compliance for banks could include informing their service providers through updated contracts or other means. Covered services are those subject to the Bank Service Company Act. Examples include sorting and posting checks and deposits, computing and posting interest and other charges and credits as well as preparing and mailing checks.
Bernard said she is surprised not to have heard more from these third parties about their requirements and how their reporting to banks will work.
"I know that there are others that share the same concern," Bernard said. "So if a bank is dependent on a very large software company for their core banking system, and most often is a cloud-based offering these days … if there's a problem with that piece of software, and their branch network is out, what is the chain of notification required, even as you're trying to resolve the problem?"
Because service providers do not have direct relationships with the federal banking regulatory agencies, it is a challenge to get the word out about the new rule, said John Geiringer, partner at Barack Ferrazzano Kirschbaum & Nagelberg LLP. He spoke during a webinar in March co-hosted by Barack Ferrazzano, the American Bankers Association, Fiserv Inc. and The Financial Services Information Sharing and Analysis Center. There are about 120,000 bank service providers nationwide compared with about 5,000 banks, Geiringer added.
Banks need to speak with their service providers about the rule.
"It'd be sensible for a banking organization to update their contracts [and] to have conversations with their service providers," Borgia said. "'Are you providing covered services or not?'" Updating contracts is not a requirement under the rule, he added. Borgia advises both banking organizations and service providers under the rule.
The definitions in the rule describe different standards for incidents that banks and service providers must report.
"There will be situations in which a service provider would be required to notify the banking organization, but the banking organization may not be required to notify the regulator," Borgia said. "So there may be a broader set of incidents that the service providers are required to notify."