S&P Global Offerings
Featured Topics
Featured Products
Events
S&P Global Offerings
Featured Topics
Featured Products
Events
S&P Global Offerings
Featured Topics
Featured Products
Events
Banking & Capital Markets
Economy & Finance
Energy Transition & Sustainability
Technology & Innovation
Podcasts & Newsletters
Banking & Capital Markets
Economy & Finance
Energy Transition & Sustainability
Technology & Innovation
Podcasts & Newsletters
S&P Global Offerings
Featured Topics
Featured Products
Events
31 Oct, 2022

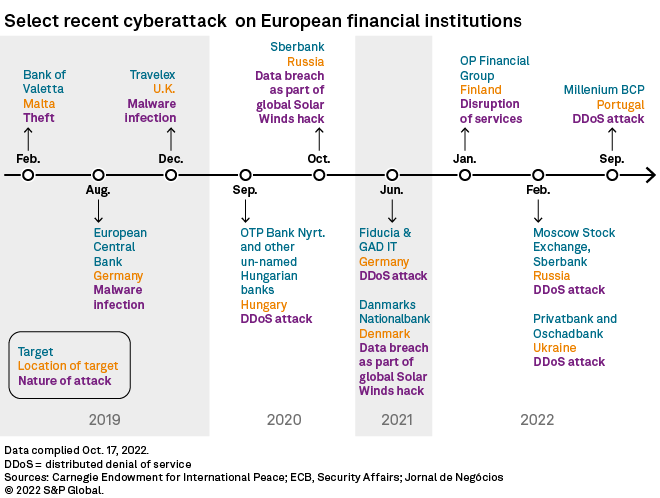
| Portugal's Millennium BCP was subject of a distributed denial of service attack in October. |
The massive and devastating Russian-led cyberattacks policymakers and industry insiders feared would hit European banks following the invasion of Ukraine have so far not materialized. But smaller and more pernicious hacks on banks, which may or may not be Russian state-linked, are on the rise.
So-called distributed denial of service, or DDoS, attacks on European banks have increased "substantially" since the start of the war in Ukraine, according to Nicole Hoffman, senior cyber threat Intelligence Analyst at Digital Shadows, a cybersecurity firm. Portugal's Banco Comercial Português SA, better known as Millennium BCP, was subject to a DDoS attack Oct. 3, resulting in a 90-minute service blackout.
DDoS attacks can involve malicious actors bombarding bank websites and apps with so much traffic that legitimate customers are left unable to access their accounts. They are usually short-lived, but industry experts say that the attacks pose a serious and ongoing risk to banks in Europe, with both revenues and reputations at stake.
"The financial sector has become a large target in Europe, specifically in countries that are considered allies to Ukraine or are seen to pose some type of threat to Russia by hacktivists," said Hoffman.

The scourge of DDoS attacks
A spokesperson for Millennium BCP declined to comment when asked about the perpetrator of the attack, but said it was "target of intense and illegitimate requests made from outside Portugal to the bank's site and apps."
In an attack following a similar typology in February, Russian military hackers temporarily knocked offline Ukrainian banks Joint-Stock Company Commercial Bank Privatbank and the State Savings Bank of Ukraine.
Russia has been on the receiving end of attacks too, with Sberbank of Russia fending off a major attack in early October, which saw its systems ambushed by 104,000 hackers from 30,000 devices operating from outside the country, local media outlet Kommersant reported, citing the bank's deputy leader, Stanislav Kuznetsov. The bank has been hit by 470 attacks this year alone, more than the total number of attacks in the past seven years combined, the report said.
Banks are generally a popular target for DDoS attacks, according to David Elmaleh, director, product management, at Imperva, a cybersecurity firm. Almost a third of all DDoS attacks recorded in the second quarter across all industries were on banks, according to Imperva's research.
What is notable about DDoS attacks is that they are often "the method of choice" for hacktivists and for cyberwarfare, Elmaleh said. Imperva found a 70% increase in DDoS attacks in March, coinciding with the invasion of Ukraine, which suggests that they are being used as a tool of warfare, he said.
"Nation-state actors are usually less interested in financial gain and instead motivated by causing disruption or using DDoS attacks as a smokescreen to smuggle malware onto a network," Elmaleh said.
Even so, the potential financial hit to banks from a DDoS attack should not be underestimated, according to Nisha Sanghani, partner at Ashurst Risk Advisory.
A DDoS attack could cost a company in the range of £140,000 and £2 million, according to research from cybersecurity firm NETSCOUT. The cost to a bank could potentially be a "significant multiple" of the highest estimate given by NETSCOUT, Sanghani said, and there is also the question of reputational damage.
"Given the risk profile of a bank, and the very public impact of reputational harm, it is likely to take a longer period of time before the site can be put back online and the bank can fully recover. Any denial-of-service attack is therefore likely to have a serious effect both at the time of the attack and in the period after," she said.
There are fears in the industry that cybercriminals could strike market infrastructure next, such as the SWIFT payments network, with dire consequences for the whole industry, Sanghani warned.
"As well as making a stand against sanctions that have been imposed, it is feared that Russia may feel that an attack on a market infrastructure such as SWIFT is a more attractive target than an individual bank given that a cyber attack on SWIFT would have a detrimental and significant impact on the global financial network as a whole," she said.
SWIFT did not respond to a request for comment.
Covert threat
The European Central Bank and the U.S. Federal Reserve Bank both warned commercial lenders in February, when an invasion of Ukraine was starting to look imminent, that they should brace themselves for an onslaught of Russian-sponsored hacks.
And when the European Commission banned seven of Russia's largest banks from the SWIFT messaging system in early March, cybersecurity experts warned that Russia could retaliate by launching crippling cyberattacks on European banks.
But so far, no Russian state-linked attacks on European banks involving theft, destruction of infrastructure or visible tampering with web content have taken place – or at least none that have been publicly disclosed.
"There is a general sense that Russian capability around cyberattacks may not be as strong as anticipated," said Cassandra Pagan, consulting principal, cyber and quantification at S&P Global Market Intelligence. "There is a lot of hacking activity around, but the Russians haven't come out in the devastating, all-guns-blazing attack that many had been expecting."
However, it is possible that Russia is playing a long game, Pagan added. Espionage, rather than destruction or disruption, could be the ultimate aim of Russian state-sponsored hacks, particularly when it comes to foreign banks, Pagan said.
In this case, dramatic attacks on banks would be counterproductive for hackers as it would make it hard to stay hidden, she said.
This is not an entirely hypothetical scenario. The SolarWinds hack, a massive cyberattack that took place in 2020 and was attributed to Russian sources, led to hackers quietly accessing the systems of major corporates and government departments across the world, and then remaining undetected for months. Among the targets was Danmarks Nationalbank, the Danish central bank.
The U.S. and the U.K. both sent signals to Russia that cyberattacks would be retaliated to in kind, which could explain the absence of material attacks so far, according to Marcos Alvarez, senior vice president, head of insurance, global financial institutions at DBRS Morningstar. It could also be that the U.S.'s abilities in this realm are stronger, he added.
"The threat is contained for now," said Alvarez. "But it is still there."
