Featured Topics
Featured Products
Events
S&P Global Offerings
Featured Topics
Featured Products
Events
S&P Global Offerings
Featured Topics
Featured Products
Events
S&P Global Offerings
Featured Topics
Featured Products
Events
Financial and Market intelligence
Fundamental & Alternative Datasets
Government & Defense
Professional Services
Banking & Capital Markets
Economy & Finance
Energy Transition & Sustainability
Technology & Innovation
Podcasts & Newsletters
Financial and Market intelligence
Fundamental & Alternative Datasets
Government & Defense
Professional Services
Banking & Capital Markets
Economy & Finance
Energy Transition & Sustainability
Technology & Innovation
Podcasts & Newsletters
Research — 13 Mar, 2023
Data privacy and protection practices within enterprises still often lack firm, dedicated leadership and responsibility despite the fact that businesses today tend to collect and maintain more sensitive/personal data than ever before. According to 451 Research's Voice of the Enterprise: Data & Analytics, Data Governance & Privacy 2022 survey, only 61.6% of respondents reported that their organization has a chief privacy officer. The general IT function still held the primary responsibility for managing data privacy and protection requirements in 41.3% of cases, with only 11.3% reporting that a "dedicated data privacy team" was at the helm of these specific efforts.
Many organizations struggle with delegating responsibilities associated with data privacy, security and cybersecurity. The Enigma conference has been hosted by USENIX — The Advanced Computing Systems Association — since 2016 with the goal of discussing data security and privacy topics far ahead of the business adoption curve. While the 2023 event held Jan. 24-26 in Silicon Valley was no exception regarding forward-looking content, it had a distinctly practical undertone for practitioners. Compared with the 2022 conference, sessions were more focused on specific challenges and how to reasonably address them, given the practical restraints of modern business environments.

In the information security sector at large, conferences tend to be highly commercial, either hosted by a specific technology provider touting its wares or subsidized by the participation and exhibition of countless others vying to do the same. Then there is USENIX Enigma. With monetary backing from only a modest number of commercial providers that have limited presence at the event, the intimate conference seeks to explore more advanced issues addressing the cybersecurity community, often looking years ahead of the business adoption curve and exploring topics that may not yet be readily addressed in the technology press. Historically, this has meant that the event often had an air of academia and theory rather than practicality.
The gathering in January was a bit different. Emerging from the haze of the pandemic, many presenters — and practitioners in attendance — were more focused on taking action. Content reflected this; while there was no lack of introspection around topics such as human rights and personal autonomy, some of the most popular sessions dug into technical details of execution and real-world use cases.

Cybersecurity: Emphasizing a common denominator concern for us all
In the practitioner realm, it can be easy to succumb to the notion of cybersecurity — or interdependent practices such as data privacy — as the technical domain of a select, trained few. At USENIX Enigma 2023, sessions sought to emphasize otherwise. In fact, cybersecurity decisions can involve and have profound effects on countless lives, livelihoods and even geopolitical stability. Data privacy and security are concerns for us all, both as professionals and citizens.
Cybersecurity, and personal data privacy in particular, are salient human rights issues worldwide. Data can be collected and leveraged by commercial or government entities for purposes that are either beneficial or detrimental to the wellbeing of the individual; rarely is systematic data collection and analysis neutral in its real-world outcome.
The conference highlighted that different populations may experience highly divergent, and potentially negative, outcomes from the same choices in commercial information security practices. A privacy-oriented product design mechanism such as self-deleting messages in a communications application may protect one vulnerable community while directly harming another. An activist might face reprisal if authorities can access their messages, while someone encountering harassment might fail to collect enough court-admissible evidence if they fail to save related messages. Design choices for privacy and security need to take into consideration the experiences and context of multiple populations, as one size rarely fits all.
Even in the U.S., where consumers benefit from a relatively stable government regime and trust in commercial entities tends to be reasonably high, concern for online data privacy and security is pronounced.
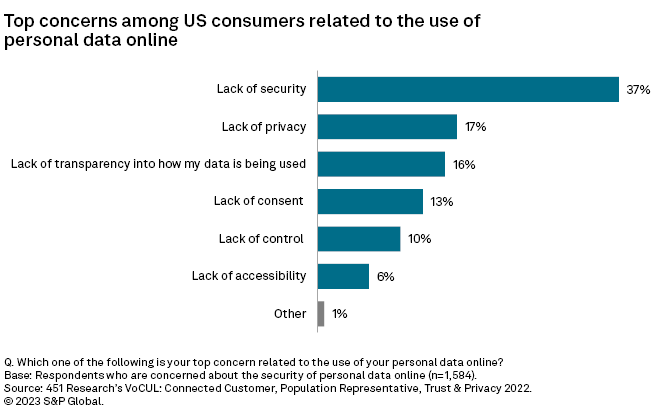
The high consumer awareness of security and privacy issues puts pressure particularly on commercial organizations that develop consumer-oriented technology to provide more granular options for users' security and privacy. The 2023 USENIX Enigma conference pointed out that making default product design choices that will benefit all populations equally is sometimes impossible, so best practices should dictate that customizable privacy and security options should be given to users whenever appropriate so that individuals may apply controls that are suitable to their own context, risk profiles and lives.
You cannot eliminate risk, but you can (carefully) rightsize your risk profile
Whether as an individual or as an organization, the quest to eliminate or eradicate risk — cybersecurity risk, privacy risk or otherwise — is generally unrealistic and counterproductive. The more appropriate approach is rightsizing risk appetite based on contextual variables, examining both cost and benefits.
For example, the secure communication tools and architectures utilized by a dissident or legitimate whistleblower in relaying sensitive information to the press may very well be too technically cumbersome or entirely unnecessary for an average citizen who wishes to share innocuous photos or messages with a family member. Likewise, for the enterprise, compounded deployment of extensive information security tooling often realistically comes with a burden on worker productivity and workflows. Businesses need to aim for balance in their security practices as humans tend to attempt to outsmart technology. Should workers become frustrated by overly cumbersome security policies and technology, it is not uncommon for them to engage in behavior that entirely undermines the purpose of those security practices, such as using unauthorized devices and technologies to get their job done, further introducing new and unanticipated risks.
For these reasons, USENIX Enigma has historically embraced the concept of usable security, or security techniques and practices that help reduce user friction rather than increase it. For individual and consumer usability, this often comes down to decisions that technology suppliers make in standardizing and embedding more default secure features and architecture. Examples include browsers deprecating third-party cookies or enabling and compelling strict HTTPs. Businesses have a trickier challenge with navigating the wide availability of enterprise security tooling options, which often have the potential to affect employee work patterns and preferences. Organizations should be looking to use new options that enhance security and usability simultaneously; for example, the rising popularity of FIDO2/Webauthn standards and other password-less authentication schemes should mutually benefit all stakeholders.
For organizations, modeling and estimating risk is an important part of rightsizing the risk appetite. However, in the realm of uncertain and probabilistic risk, businesses should avoid placing too much faith in numerical estimates and models. Even insurance companies with their actuarial capabilities struggle to accurately quantify cyberrisk. Many of the probabilities related to risk in cybersecurity are inconsistent, unknown or subject to hidden variables. Often, cybersecurity business risk probabilities are estimated based on past incidents that have already occurred and been reported via official channels, creating bias against the countless events that were never reported or documented. Even academic cybersecurity research suffers from challenges around reproducibility and consistent availability of representative data.
Sessions at the conference highlighted that organizations need to use caution, particularly when using risk probability models to estimate potential financial impacts of cybersecurity incidents. What may appear to be an extremely small or extremely large calculated financial impact of a potential risk could be the result of multiple compounding estimates with wide variability or uncertainty. Furthermore, distortions in business metrics can have a direct impact on cybersecurity optimization efforts. As organizations strive to become more data-driven, it is not uncommon for them to collect what may be weak or misleading proxies for the outcomes they actually wish to measure. Such practices can yield poorer business results than the use of no metrics at all. Confounding activity with progress can have devastating effects. USENIX Enigma 2023 emphasized that metrics — in the realm of security — need to be defined, collected and interpreted with a critical mindset.
So if it's broken, let's fix it
Sessions at the event were divided into thematic tracks, typically alternating content between groups of presentations focused on higher-level societal implications of cybersecurity practices and technology use, and deeper technical discussions of specific challenges or opportunities. What nearly all the sessions shared this year was a practical element: best practices wrought from business experience, vulnerabilities identified in existing architecture or systems, advice on communicating objectives to organizational stakeholders, likely implications of emergent technologies, or introspective examinations of current information security research methods.
Live audience Q&A played an important role in the on-site sessions and offered a gauge of interest among attendees, many of whom were also speakers and presenters themselves. Some of the sessions that garnered the most traction were related directly to existing or emergent technology and its potential vulnerabilities or implications that could reasonably be addressed by contemporary practitioners in their own organizations.
Nearly all sessions this year had an ultimate practical element. However, some of the presentations and panels that were particularly focused on applied techniques and advice touched on topics such as quantum computing's potential role in cybersecurity, the brittle state of web public key infrastructures, memory safety vulnerabilities, current detection methods for malware, use of open-source tooling, and ongoing protection techniques available to journalists and whistleblowers.
Other common themes were the appropriate and proportionate use of automation techniques in cybersecurity as well as the alignment of organizational cybersecurity objectives and cultural motivational factors for organizations looking to bolster their efforts. The conference also had an entire track dedicated to topics pertaining to organizational interpretation and execution of data privacy requirements.
Data privacy, security and cybersecurity at large are not just technological problems to be nominally solved with a single new tool or piece of software, however. The relative low profile of USENIX Enigma's commercial backing reinforces this. These are complex, multivariate issues, both for individuals or citizens and for organizations looking to properly steward information.
There are occasionally contradictory cases where a regulatory cybersecurity or privacy requirement may conflict with others, or where a security design intervention may even potentially pose harm to a vulnerable population, forcing difficult ethical choices. It behooves professionals in this field to be highly collaborative and well rounded in their skills rather than just focused on technicalities, as interpretation of cultural and business context often supersedes the nuts and bolts of execution. For security to progress, testimony from contrarians is often necessary.
Last year's conference waxed poetic on esoteric societal harms and pitfalls in the security and privacy realm: "What actually constitutes factual information online?" (Spoiler alert: human society cannot agree). But at USENIX Enigma 2023, the focus was more on actionable advice and techniques relevant to practitioners. The cybersecurity rubber was hitting the road.
This article was published by S&P Global Market Intelligence and not by S&P Global Ratings, which is a separately managed division of S&P Global.
451 Research is part of S&P Global Market Intelligence. For more about 451 Research, please contact 451ClientServices@spglobal.com.
